(далее…)
Блог
-
A Review of "Building Secure Products and Solutions"
Historically speaking, many applications were designed to be overly trusting. For example, early personal computers were not networked and it was assumed whoever was in front of them owned them and should be able to do whatever they wanted with them. Another example is that in the early days of the Internet,
(далее…) -
Deliberately Insecure Web Applications For Learning Web App Security
Over the last few months I’ve been teaching free classes for the ISSA Kentuckiana chapter in Louisville Kentucky. After doing one on Nmap and another on Sniffers, I talked it over with my buddies Brian and Jeff and decided that the next one should be on web application vulnerabilities.
(далее…) -
1337 in the Library: Obtaining your information security education on the cheap
The two quotes above were my inspiration for writing this article, along with the fact people keep asking me «How do I get started in security». Well, if you’re asking for career advice I’m not your man, but on the learning side of things I think I have a few tips I can give you.
(далее…) -
Obfuscated 4chan.gif/Invasion.gif/SYS.JSE Decoded and Removal
t of encoding it was using, and folks pointed me to the post at the SAN Internet Storm Center:But that had few detail on how the encoding was done. Byte_Bucket from Pauldotcom pointed me at a tool called «Windows Script Encoder» from Microsoft that seems to be what was used. After doing some checking, the encoded part of the JSE starts with #@~^ , which is also what the MS tool creates.
(далее…) -
XSS, Command and SQL Injection vectors: Beyond the Form
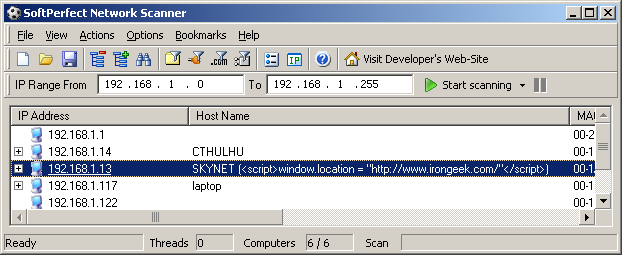
Active Directory Not to beat a dead horse, but what about all of the fields you can fill out on an Active Directory or LDAP object? Now that I think about it, maybe it’s time for me to update my ADS Reaper tool.
Application Names and Metadata Got an asset tracker that lists the software installed on a machine to a lovely HTML report? Does the assets tracking software look at the metadata in files? That could be another possible vector.
Banners
Is your custom scanning software logging the banners it sees on open ports? What if the banner has a little malicious XSS?
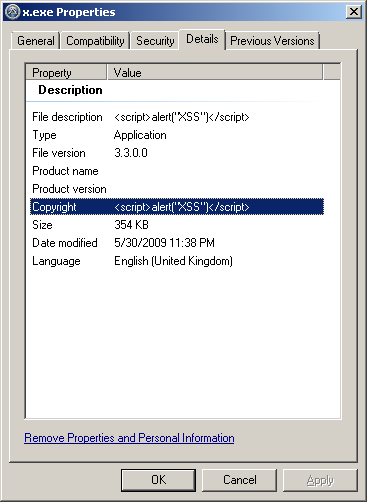 Conclusion
ConclusionGranted, many of these possible attack vectors are hypothetical, and depend on reporting tools not sanitizing data. Still, I hope this short article makes the wheels in your head start grinding away at new way of thinking when it comes to injection attacks. For more ways to mangle XSS to get it past filters, check out RSnake’s excellent cheat sheet:
http://ha.ckers.org/xss.html