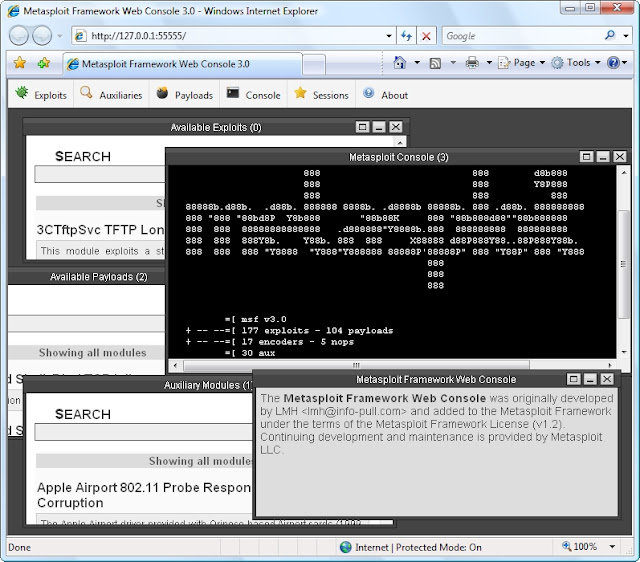
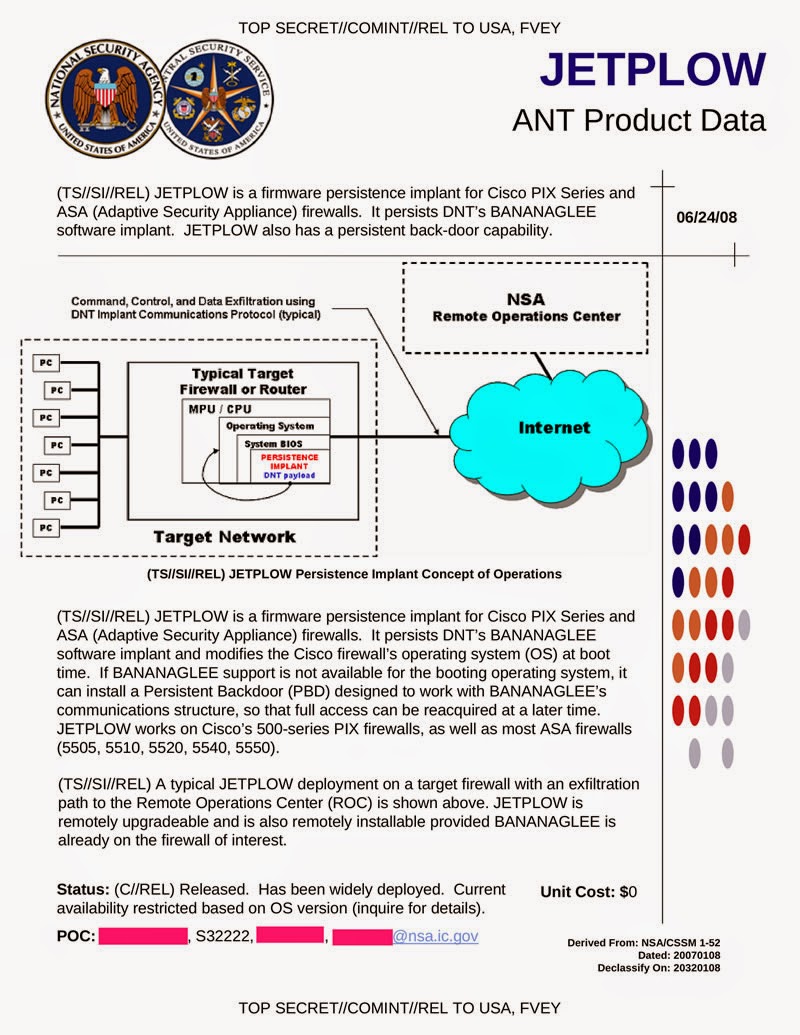
Attackers have been observed substituting Cisco’s IOS bootstrap with a malicious ROMMON image after first accessing the company’s IOS devices, according to an alert issued by
Cisco Product Security Incident Response Team (
PSIRT).
The PSIRT said it began contacting customers regarding the “evolution” detected in attacks launched against its IOS Classic platforms.
“In all cases seen by Cisco, attackers accessed the devices using valid administrative credentials and then used the ROMMON field upgrade process to install a malicious ROMMON,” the alert said. Once the device was rebooted they could control its behavior.
Utilizing a malicious ROMMON provides attackers an additional advantage because infection will persist through a reboot,” the PSIRT wrote, explaining that since the miscreants didn’t exploit a vulnerability but rather acquired valid admin credentials or were able to gain physical access to the device to carry out the attack, that a CVE ID wouldn’t be assigned.
“The ability to install an upgraded ROMMON image on IOS devices is a standard, documented feature that administrators use to manage their networks,” the alert said.
The team referred users to trio of white papers that it said would help users understand threats against Cisco IOS devices as well as how to remediate them.

 Скачать
Скачать