Блог
-
NSA Backdoors in Cisco Routers
The more I read about this NSA scandal (and yes, I do consider it a scandal) the less I trust US-based hardware and software companies. There is no reason for anyone to doubt that all Cisco hardware comes with a backdoor. Since such backdoors most likely exist it is a matter of time before hackers discover and exploit them. This has already happened to Microsoft a number of times and there is no reason it could not happen to Cisco. We no longer trust any of our Cisco hardware and have already started researching network alternatives.This is no longer a crackpot conspiracy theory, it is reality.In all liklihood we may use a series of firewalls to further insulate our network from intrusion. To keep costs down we may keep our existing Cisco hardware in this topology, but we will not replace it with Cisco hardware when it fails or needs to be upgraded. I am doing the same with my home network.Over the past few months we have already moved all of our email to secure overseas servers and changed all of our antivirus software from McAfee to AVG and Avast. We are also researching Linux distros to replace Microsoft.If Cisco wants to protect their brand they need to either take a stand or see their market share continue to erode. Surely there is ONE CEO at an American company that will take this stand and be a hero rather than continue to be a lap dog. -
12 True Tales from Gen Keith Alexander about Creepy NSA Cyberstalking
The NSA has released some details of 12 incidents in which analysts used their access to America’s high-tech surveillance infrastructure to spy on girlfriends, boyfriends, and random people they met in social settings. It’s a fascinating look at what happens when the impulse that drives average netizens to look up long-ago ex-lovers on Facebook is mated with the power to fire up a wiretap with a few keystrokes.One such analyst working on foreign soil started surveillance on nine phone numbers belonging to women over five years, from 1998 to 2003. He “listened to collected phone conversations,” according to a letter from the NSA’s Inspector General to Senator Charles Grassley released today. The unnamed spy conducted “call chaining” on one of the numbers — to determine who had called, or been called from, the phone — and then started surveillance on two of those numbers as well.
He was thwarted only after a woman he was sleeping with reported her suspicions that the analyst had been listening to her phone calls. The analyst resigned.In 2011, another civilian NSA employee abroad “tasked” the telephone number of her boyfriend and other foreign nationals. When she was asked about it, she claimed it was her practice to query the phone numbers of people she met socially to make sure she wasn’t talking to “shady characters.” (Because you wouldn’t want that.)In 2005, a military member used his first day of access to run six e-mail addresses belonging to an ex-girlfriend.Some of the abuses were referred to the Department of Justice, but none resulted in prosecution. The complete letter to Grassley follows. -
How to build the BGP UPDATE packet
bgp-update-create is a small program used to generate the payload of a BGP UPDATE message. It was written to test if routes could be injected in a BGP conversation between two routers.It’s usage is very simple; it takes three parameters:
—as: Autonomous System number
—nexthop: Host name or IP address of next hop
—destnet: Network number/prefix to advertise
To use it with tcphijack you just pipe its output to tcphijack, like in:
sudo bgp-update-create —as 2 —nexthop 1.1.1.1 —destnet 2.2.2.2 | tcphijack […]
or just send its output to a file and then use tcphijack’s -P switch to specify a payload:
bgp-update-create —as 2 —nexthop 1.1.1.1 —destnet 2.2.2.2 > payload.dat
sudo tcphijack […] -P payload.dat
bgp-update-create is built at the same time as tcphijack (by typing «make»), the header files used by bgp-update-create.c come from the Zebra project.
BGP Update Create download
-
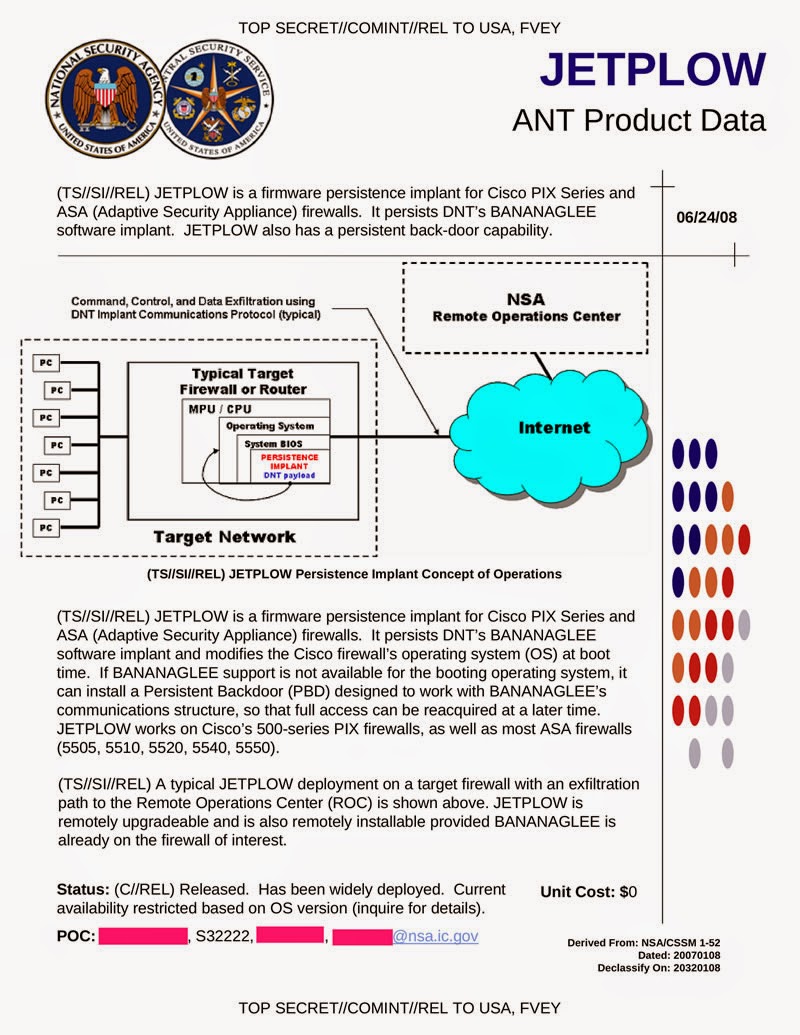
How to find the JETPLOW on Cisco firewalls installed
JETPLOW is a firmware persistence implant for Cisco PIX Series and ASA (Adaptive Security Appliance) firewalls. It persists DNT’s BANANAGLEE software implant. JETPLOW also has a persistent back-door capability.JETPLOW is a firmware persistence implant for Cisco PIX Series and ASA (Adaptive Security Appliance) firewalls. It persists DNT’s BANANAGLEE software implant and modifies the Cisco firewall’s operating system (OS) at boot time. If BANANAGLEE support is not available for the booting operating system, it can install a Persistent Backdoor (PDB) designed to work with BANANAGLEE’S communications structure, so that full access can be reacquired at a later time. JETPLOW works on Cisco’s 500-series PIX firewalls, as well as most ASA firewalls (5505, 5510, 5520, 5540, 5550).
A typical JETPLOW deployment on a target firewall with an exfiltration path to the Remote Operations Center (ROC) is shown above. JETPLOW is remotely upgradable and is also remotely installable provided BANANAGLEE is already on the firewall of interest.
Status: Released. Has been widely deployed. Current availability restricted based on OS version (inquire for details).